Windows Information Protection and Folder Redirection – 0x807c0008
We are rolling out Windows Information Protection (WIP) for one of our clients. WIP will be deployed for MAM and MDM devices
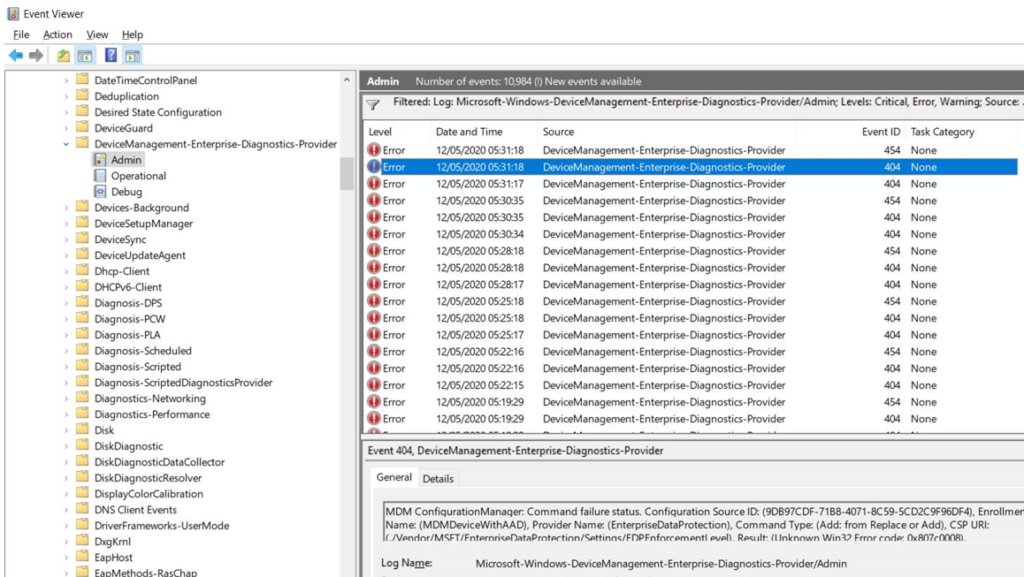
WIP was not deploying at all for certain devices and there was very little information why except for one Event Log error:
MDM ConfigurationManager: Command failure status. Configuration Source ID: (9DB97CDF-71B8-4071-8C59-5CD2C9F96DF4), Enrollment Name: (MDMDeviceWithAAD), Provider Name: (EnterpriseDataProtection), Command Type: (Add: from Replace or Add), CSP URI: (./Vendor/MSFT/EnterpriseDataProtection/Settings/EDPEnforcementLevel), Result: (Unknown Win32 Error code: 0x807c0008).
Additionally we were seeing registry keys with _Dirty appended to the end like this:
HKLM\SOFTWARE\Microsoft\PolicyManager\current\device\DataProtection
EDPShowIcons_Dirty
Interestingly, we could get WIP to apply if a Local Administrator Account logged on directly to the Workstation at least once, and it would stay sticky – even though the Domain account logging in previously was a Local Workstation Admin
Here is the fullback ground of our set-up:
- Workstation was Windows 10 Enterprise fully patched
- Workstation was Azure AD Hybrid Joined via AAD Connect from On-Premises AD via AAD Connect
- Workstation is auto-enrolled via GPO making it a Corporate Device
- Workstation is a single user machine
- Only one user has ever logged on, and that same user is the user enrolling it
- That user has local Admin rights
- Workstation gets successfully enrolled and is being checked for Compliance
- Workstation is receiving the WIP MDM Policy. We can see DataProtection and NetworkIsolation
- Workstation does NOT WIP successfully applied
- The MDMDiagReport.html file shows that the Managed policies are being written correctly for the Area DataProtection: EDPShowIcons, EnterpriseProtectedDomainNames and NetworkIsolation: NeutralResources, EnterpriseCloudResources
- We can see the registry key at HKLM\SOFTWARE\Microsoft\PolicyManager\current\device\DataProtection going down, but they get an _dirty appended to the relevant keys
- We tries several times to unenroll and reenroll the device, including deleting from Intune and AzureAD and starting again
- A non Domain Joined device getting MAM does successfully get WIP enabled
This is the Microsoft answer from support
WIP isn’t turned on for employees in your organization. Error code 0x807c0008 will result if WIP is deployed by using Microsoft Endpoint Configuration Manager.
This is essentially limitation of WIP :-
Support article :-
Off to that technote and we see in that article a table, and one of the rows has this:
Limitation
WIP isn’t turned on if any of the following folders have the MakeFolderAvailableOfflineDisabled option set to False:
- AppDataRoaming
- Desktop
- StartMenu
- Documents
- Pictures
- Music
- Videos
- Favorites
- Contacts
- Downloads
- Links
- Searches
- SavedGames
How it appears
WIP isn’t turned on for employees in your organization. Error code 0x807c0008 will result if WIP is deployed by using Microsoft Endpoint Configuration Manager.
Workaround
Don’t set the MakeFolderAvailableOfflineDisabled option to False for any of the specified folders. You can configure this parameter, as described here.
If you currently use redirected folders, we recommend that you migrate to a file synchronization solution that supports WIP, such as Work Folders or OneDrive for Business. Additionally, if you apply redirected folders after WIP is already in place, you might be unable to open your files offline. For more info about these potential access errors, see Can’t open files offline when you use Offline Files and Windows Information Protection.
Very helpful Microsoft speak with double, double negatives and so on. So reading this line: Don’t set the MakeFolderAvailableOfflineDisabled option to False means make it “Do make it True”, meaning that Offline files are Disabled.
Additionally the terminology isn’t quite right with respect to GPOs, as the GPO options are Default, Enabled and Disabled. So the way to go here is in fact – Enabled.
Yes, we had redirected folders enabled via GPO. We were re-directing them to OneDrive. This was because before OneDrive improved with Known Folder Moves (KFM), this was the best way to get user data automatically saved into OneDrive, and therefore backed up in the Cloud. But there is still an issue because at time of going to print, KFM only targets Desktop, Pictures and Documents meaning that Downloads, Music and Videos are not represented so we are having to maintain the GPO for those.
The two GPO settings you need to work with are:
User Configuration/Administrative Templates/System/Folder Redirection
- Do not automatically make redirected folders available offline
- Do not automatically make specific redirected folders available offline


What should the GPO look like?
Do not automatically make redirected folders available offline
If you enable this policy setting, users must manually select the files they wish to make available offline.
If you disable or do not configure this policy setting, redirected shell folders are automatically made available offline. All subfolders within the redirected folders are also made available offline.
Thus, this needs to be set to Enabled

Do not automatically make specific redirected folders available offline
If you disable or do not configure this policy setting, all redirected shell folders are automatically made available offline. All subfolders within the redirected folders are also made available offline.
Thus, this needs to be set to Enabled and choose the folders to set it for.
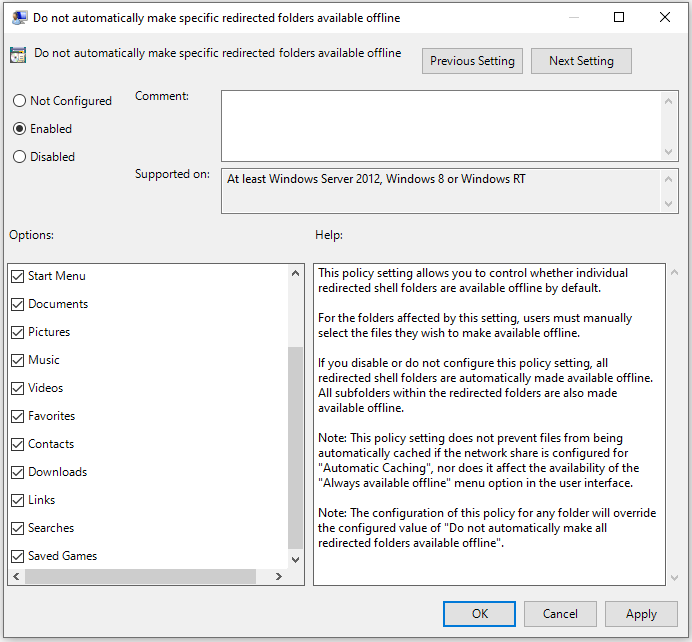
At time of writing we have set: Do not automatically make redirected folders available offline = Enabled, but are still working with Folder Redirection for Music, Videos and Downloads.
In your environment you might need/want to experiment with Do not automatically make specific redirected folders available offline
After this change WIP finally kicked into life on the next GPUpdate and Intune sync!
As always, have to say it took a longer time than we would have liked to get to the bottom of this, and whilst we were lucky as a team to be responsible for the Group Policy and Intune deployments, if you have separate IT functions it might take longer to get the bottom of this.
Case closed.