Microsoft 365 Tenant Hardening: The No-Nonsense Basics
From enforcing MFA to scaling up with E5-level protections, this guide breaks down the no-nonsense steps every organisation should take to secure their environment.
Whether you’re a scrappy start-up, a mid-sized mover, or a sprawling enterprise, one thing’s universal: your data needs guarding. And not just a polite lock on the front door. Think steel vault, motion sensors, and a rottweiler named MFA.
From usernames and passwords to intellectual property, client records, and employee info – if it lives in your Microsoft 365 tenant, it’s a target.
Fortunately, Microsoft gives you a decent security toolkit out of the box.
- Business Basic – Core protection for email and user accounts
- Business Standard – Adds device management and data safeguards
- Business Premium – Advanced SMB security with device and threatprotection
But if you want the good stuff – the kind of tenant hardening that actually keeps attackers out – you’ll need to level up your licensing.
- E3 – Enterprise baseline with identity, security, and compliance
- E5 – Full advanced security, threat intelligence, and compliance
Microsoft 365 Licensing Matrix
Check out the M365 Feature Matrix to see what lights up with each license tier.
From Business Premium to E3: The First Step Up
- Azure AD Premium P1
Conditional Access, self-service password reset with writeback, and Hybrid Identity. Basically, it stops your users from being the weakest link. - Microsoft Intune
With E3 you start layering in more enterprise-scale device management and security. - Information Protection
You get sensitivity labels and basic data loss prevention (DLP) beyond what’s possible in lower tiers.
From E3 to E5: Where the Real Muscle Lives
Advanced Threat Protection
- AAD Premium P2
Risk-based Conditional Access, Identity Protection, and Privileged Identity Management (PIM). Translation: smarter access control and fewer “whoops” moments. - Defender for Office 365 Plan 2
Safe Attachments, Safe Links, and threat hunting tools. Because clicking random links is still a thing. - Defender for Endpoint Plan 2
EDR, threat hunting, and automated remediation. Like having a cyber bloodhound on patrol.
Insider Risk & Compliance
- Defender for Cloud Apps (MCAS)
Full CASB capabilities. Monitor, control, and sleep better at night. - Insider Risk Management & Advanced eDiscovery
For when things go sideways and you need receipts.
Strike a balance: Yes, you need to balance security with usability and cost, but there are some absolute, non-negotiable basics that every tenant should have in place—no excuses.
Security Posture: What’s Yours?
Your “security posture” is just a fancy way of saying: how seriously do you take protecting your stuff? If you’re in a regulated industries like finance, healthcare, legal and others then you’ve got acronyms like FCA, GDPR, SEC, SOX, and HIPAA breathing down your neck. That means your posture needs to be more Iron Man than SpongeBob.
Even if you’re not in a regulated space, you still owe it to your clients, staff, and stakeholders to keep their data safe. Charities, not-for-profits, cupcake shops – everyone’s got something worth protecting.
The Security Maturity Journey: From Cupcakes to Cryptography
I often use this analogy: imagine a scale from a family-run cupcake business to a government agency with black helicopters. Their security needs are wildly different, but there’s a shared baseline for tenant hardening that everyone should cover.
Multi-Factor Authentication: The Hill to Die On
If you take one thing from this post, let it be this: Multi-factor authentication (MFA) is not optional. It’s the single most effective control you can implement – no cost, massive impact. MFA should be the first, most urgent step in your security journey.
Microsoft once said MFA blocks 99.9% of account compromise attacks. That statistic has been memed to death and somewhat of a security industry cliché, but the truth still holds. Without MFA, you’re basically leaving your tenant’s front door wide open with a “please don’t hack me” sign.
MFA isn’t a silver bullet—but it is the foundation. Without it, every other security measure you deploy is compromised from the outset.
Passwords Alone Are Not Enough
And no, your 24-character password with symbols and emojis isn’t enough. Even complex passwords get phished, guessed, or stolen.
Wondering if your password has been compromised? Have a look here: https://haveibeenpwned.com/
Have I Been Pwned is a free resource for anyone to quickly assess if they may have been put at risk due to an online account of theirs having been compromised or “pwned” in a data breach.
MFA is your second line of defence – and it needs to be phishing-resistant. Basic methods like SMS or voice call can be bypassed via SIM-swapping or phishing proxies. That’s why Microsoft now strongly recommends phishing-resistant MFA:
- Windows Hello for Business
- Authenticator app with number matching
- FIDO2 security keys
- Certificate-based authentication (CBA)
Administrator Accounts
Administrators should be provided with dedicated admin accounts that do not carry permanent administrative rights. Access should be secured with phishing-resistant MFA. When elevated privileges are required, administrators must use Privileged Identity Management (PIM) to assign the least privilege necessary for the shortest possible duration. Standard user accounts should never be elevated to perform administrative tasks.
From Baseline to Advanced Compliance
Microsoft 365 provides a scalable security framework that allows businesses to start with essential protections and evolve into advanced, compliance-driven security postures. Here’s how that journey looks:
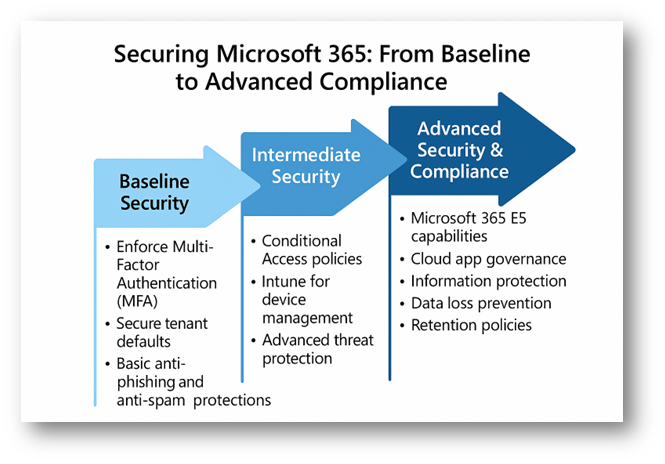
Baseline Security (Minimum for All)
- Enable Security defaults in Entra ID to block legacy authentication and strengthen sign-in security. https://learn.microsoft.com/en-us/entra/fundamentals/security-defaults
- Enable MFA for everyone – yes, even guests. This is your digital deadbolt.
- Configure anti-phishing and anti-spam in Exchange Online.
- Patch regularly and enforce strong password policies.
Intermediate Security (Growing Businesses)
- Conditional Access policies Control access based on user risk, device compliance, and location.
- Intune Apply App Protection and Device Compliance Policies.
- Privileged Identity Management (PIM) to control and audit administrative access.
- Defender for Office 365 Safe links, safe attachments, and threat protection.
Advanced Security & Compliance (Enterprise and Regulated Industries)
- Microsoft Defender for Cloud Apps (MCAS) for cloud app governance and threat detection.
- Information Protection labels (AIP) to classify and encrypt sensitive data automatically.
- Data Loss Prevention (DLP) policies to prevent accidental or malicious sharing of confidential information.
- Retention policies and records management to meet legal and regulatory data retention requirements.
- Privileged Identity Management (PIM) to control and audit administrative access.
- SIEM/SOAR solutions for advanced monitoring, incident response, and reporting.
Final Thoughts
By starting with the basics and scaling up, you can align your Microsoft 365 security posture with your business needs, regulatory obligations, and risk appetite. Whether you’re baking cupcakes or building rockets, the tenant hardening journey starts with locking the front door.
- MFA everyone, all the time, from everywhere.
- Utilize Privileged Identity Management to control administrative access.
- Enforce Device Compliance through Intune
- Use Risk based policies in Conditional Access


