Hmmm…can’t find that team
We’re seeing renewed issues with Microsoft Live ID or Microsoft Personal accounts interfering with new corporate identities when an organisation starts is Microsoft Cloud/Teams journey. Users cannot access resources (documents/Teams) which they have been given permission, or join Microsoft Teams due to security restrictions, like conditional access or guest account settings.
Conrad provided an excellent account of his issues a few years back before Microsoft Teams was around (https://neroblanco.co.uk/2017/02/microsoft-account-dilemma/) which is also worth a read as a primer on this article.
The challenge I will focus on is for Microsoft Teams (and sharepoint) which has made the Microsoft Personal account issue more wide spread as people are sharing documents and accessing teams more collaboratively without using the correct account from the outset.
Not only is there a challenge with logging onto a team with the correct account, if someone uses their Personal Microsoft account to do this for the first time, then they are unable to back track on that, only the organisation administrators which sent the access request can. This is a very specific scenario, but a handy one to be aware of, which I will explain in this blog.
The account challenge creates a bad experience for the consumers of the data you’re trying to share, and also a security risk where you are not confident you are sharing data with another business, if someone at that business leaves.
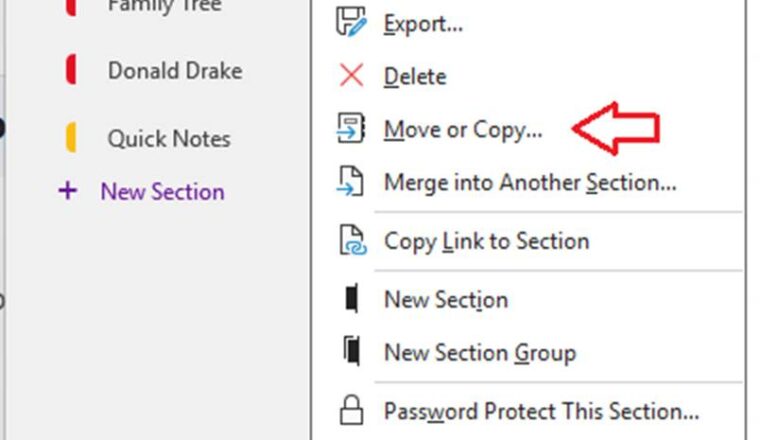
Companies have expedited their cloud journey and sometimes we see that there are persistent issues accessing teams. Here is one such error:-
“Hmmm…can’t find that team Looks like the team or channel you are looking for doesn’t exist. Please contact the team owner, or try again later.”
Furthermore with Corona Virus / Covid 19 Azure/MS Teams is having a massive take up.
https://www.businessinsider.com/microsoft-teams-coronavirus-daily-active-users-2020-3?r=US&IR=T
“Microsoft Teams added 12 million daily active users in a single week amid the coronavirus crisis, bringing it up to 44 million total”
Can only access a Microsoft Team with a Microsoft Personal account.
This stems from people linking their corporate identity (before the organisation had Azure Active Directory or a Microsoft tenant or Microsoft 365 account) to a Microsoft Live ID / Personal account (a @outlook.com or @hotmail.com).
For example if I try to add my corporate email account to my Microsoft Live ID account I cannot do it. (Microsoft started preventing this September 2016)
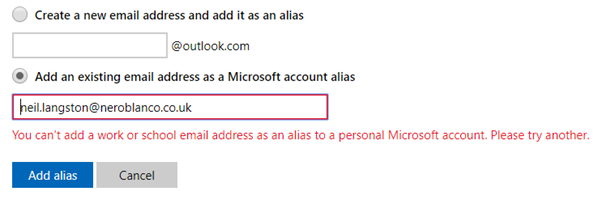
“You can’t add a work or school email address as an alias to a personal Microsoft account. Please try another.”
This is only disabled if the organisation has registered their domain with an O365 tenant.
However, if I try a random email address not associated to any Microsoft tenant, I can successfully do this…
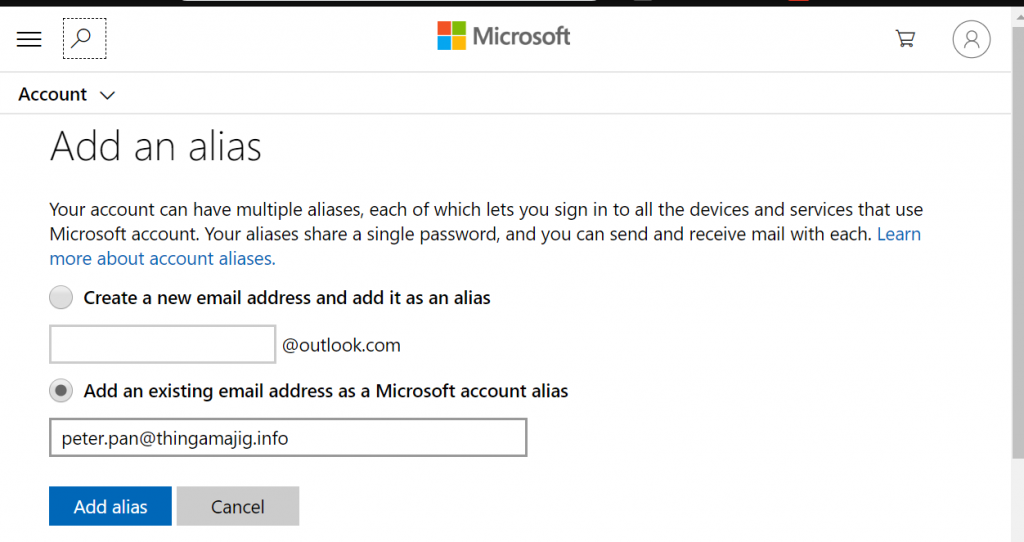
After verification it’s now added

You can imagine someone might have done this up to 10+ years ago using their corporate email address.
Then on a test team I can add this into the access
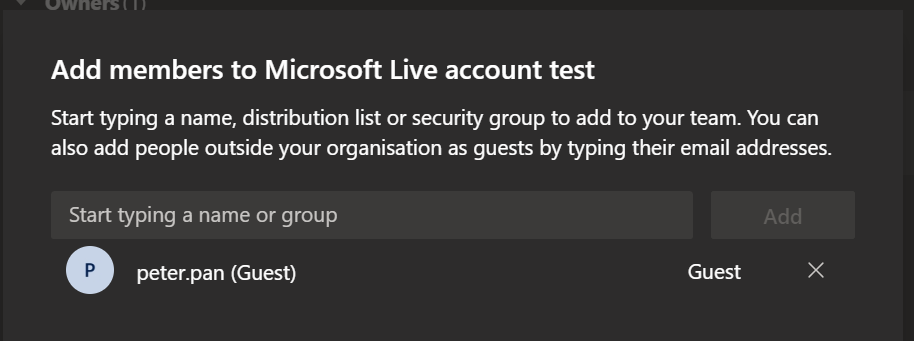
Peter received the email accordingly (ignore that it’s in outlook, I have forwarding enabled)
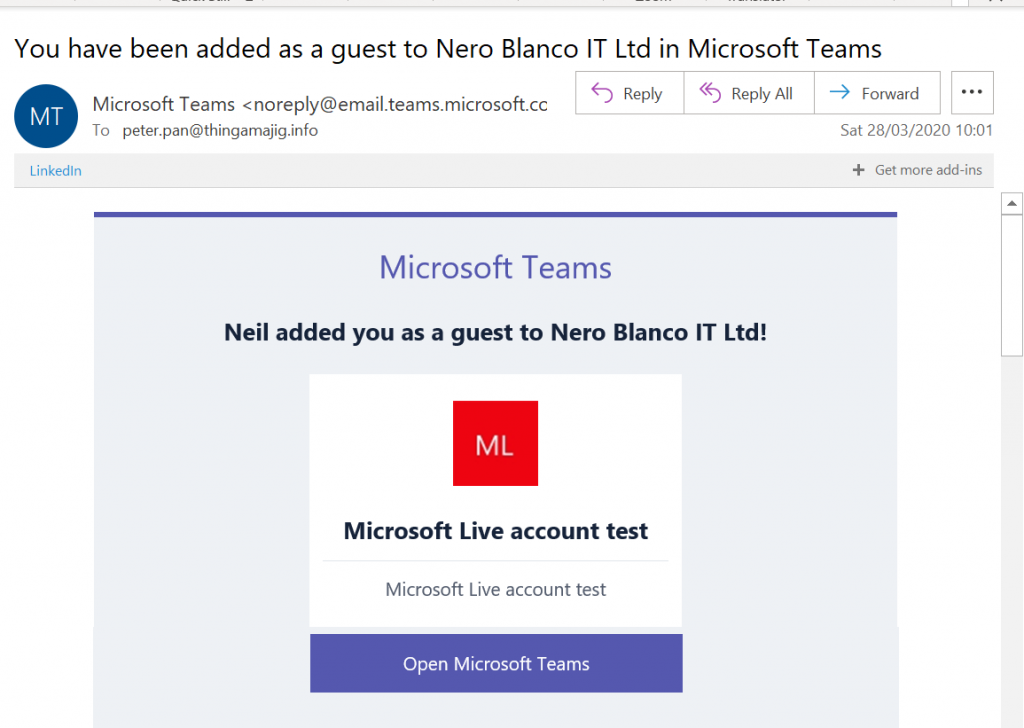
This account then gets added into Azure Active Directory (AAD) as an “Invited user”, this is because any user added to a resource like a document or team will be added into the organisations AAD to have continuity of access. Microsoft at this juncture has not assumed which type of account this recipient will use to access the resource.
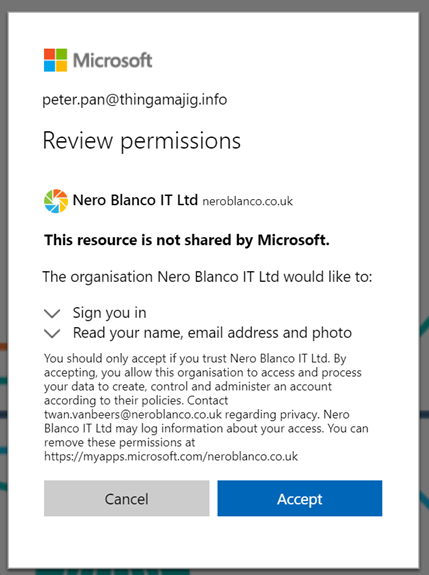
Peter then tries to access access the team…..
I did come across this prompt, and had to temporarily change my primary alias in the Microsoft Live ID/Personal dashboard to the Peter Pan address to get this demo to work. It’s probably fairly normal for the personal account to be the primary, as some people may have had their work email address for a very long time.
Once completed Peter was allowed access to the team
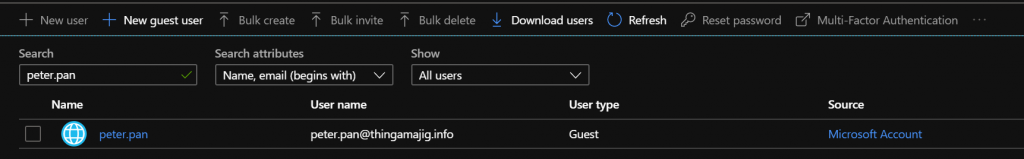
If we now look at the account in Nero Blanco AAD its now a “Microsoft Account”, or sometimes know as a Live ID or Personal Microsoft account.
Where does the problem start to creep in?
Going forward, Peter will always have access to this team (or another allocated resource to his email address) in the Nero Blanco Tenant even if he leaves the organisation his work email address is associated to.
Down the line, the admin at this organisation could add the domain to their tenant as part of moving forward with their cloud strategy.
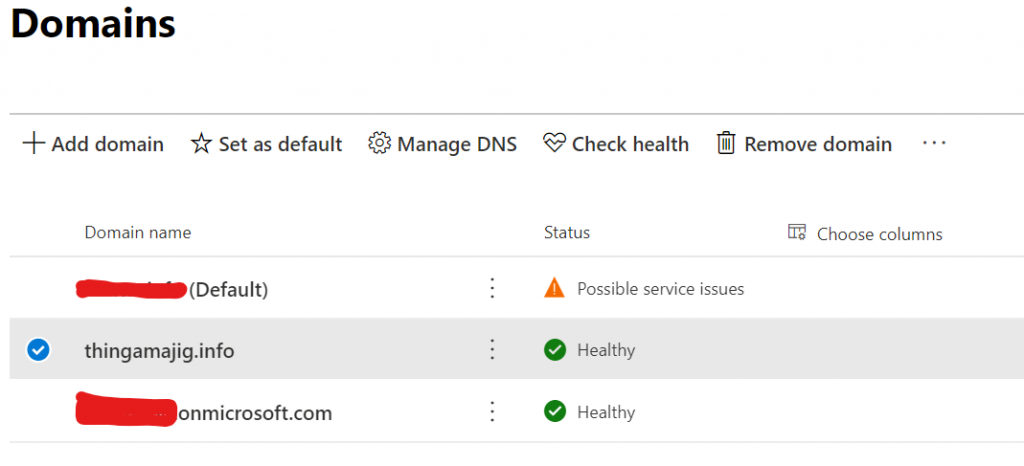
In the example snapshot below, I have a spare tenant, here I have added the domain to this tenant, this simulates the domain being part of AAD for an external organisation.
I’ve also added Peter as a new user with only the “Microsoft Teams Exploratory” license for the purposes of this demo. This also enabled teams in this tenant.
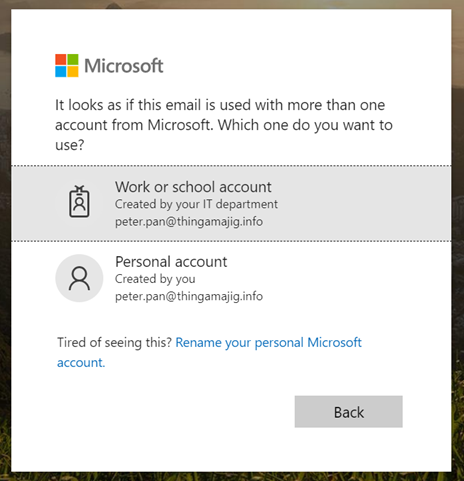
Now, if you give Microsoft a couple of hours to update, if you try to access teams again, you’ll get the choice between the two account, corporate or personal
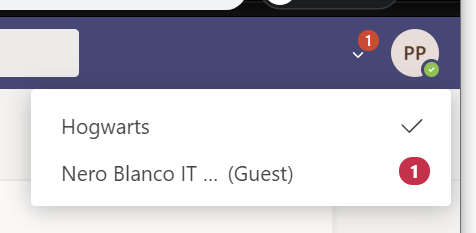
If you log into the corporate side “Work or school account”, you interestingly still have the Nero Blanco team available as the alternate organisation. Perhaps this is some caching.
But you’re unable to access it. Great!
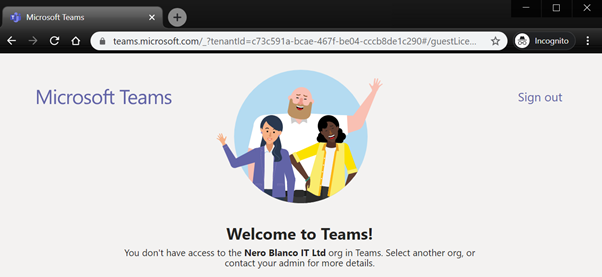
However, if you try the personal account, success.
Going forward, any resource which Peter gets added to in Nero Blanco’s tenant will be linked to his personal account rather than corporate even if he leaves his company. As it can only be the account listed for that address in Nero Blancos AAD.
Also, Peter will have a bad experience of having to switch between accounts in the browser and on his full fat client to access different resources.
Furthermore, if the sending or receiving organisation makes any security changes on their devices, sharing policies or tenant restrictions, this could restrict access to personal accounts even further causing much confusion.
So, how do we fix this?
Firstly, the user should remove their corporate identity from their personal account. This is for due diligence, simplicity, security and cleanliness reasons, rather than technical. Im sure most of the steps could be achieved without this.
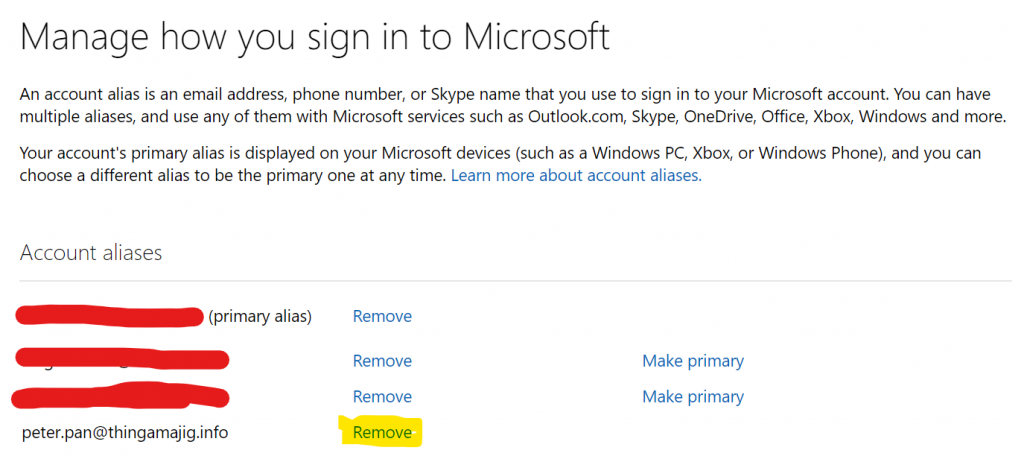
Once you’ve done this, if you sign back into teams, you’re not presented with which account dialogue to use any more. You can only use the “Work or school account” corporate/work one.
However, the teams you had access to, have disappeared from the organisations, because it was a different account which had access.
The natural thing to do as a user might be to ask the organisation (Nero Blanco) to delete, then re-add you back into the team membership. However, this does not work as Peter is still in Azure AD. Peter will receive the invite email to his corporate Exchange Online mailbox, and not be able to use it unless he still had his personal account setup.
As a user, you can actually view the type of account Peter has in AAD.
https://portal.azure.com/#blade/Microsoft_AAD_IAM/UsersManagementMenuBlade/AllUsers
It is possible for Peter to review his own account type in the tenant too, buy going to the URL above. (even if he has a Microsoft Personal account)
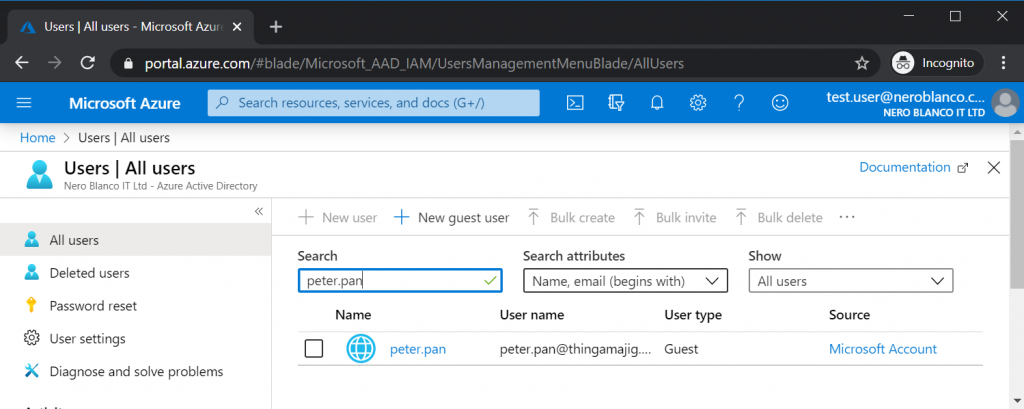
However, they will not have access to do anything to the external user account, like for example, delete.
You now have to ask your tenant admins to delete Peter from AAD, which will also remove Peter’s access to everything in your tenant, (everything from onedrive, sharepoint, to teams) that action is not recoverable. (without lots of scans with complex powershell to save and then re-apply permission – Nero Blanco have ways to do this!)
If you now try to add Peter from the name cache, you get an error.
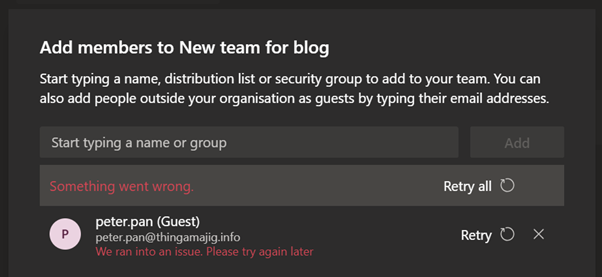
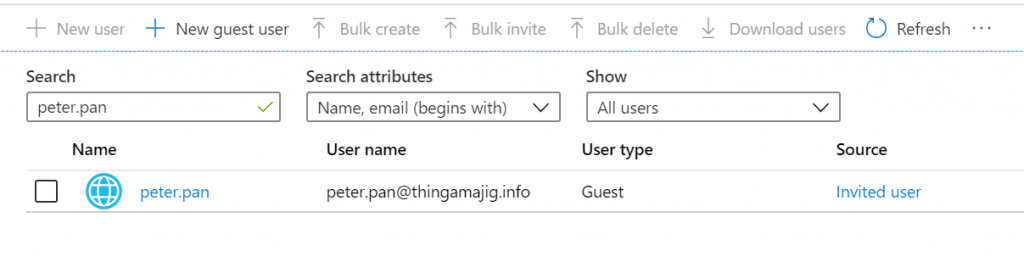
It may take an hour or two for the person to disappear from all the Teams memberships, but it will happen eventually. You can try via the browser which will be quicker and once done, Peter has returned into AAD as an Invited user, as well as receiving a fresh teams invite.
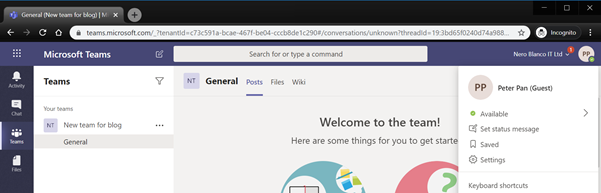
Now when Peter signs in again using the corporate account, he can access the team.
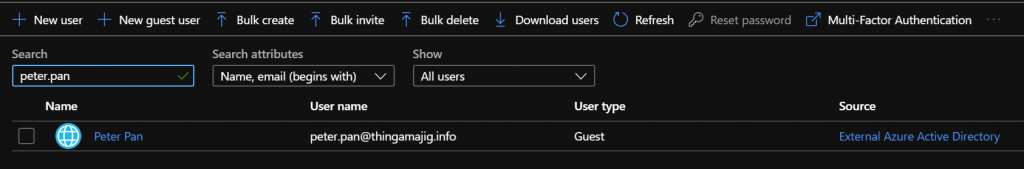
Peter is now an account type/source of “External Azure Active Directory” and can be re-added to all the other resources again. Remember, this could be any workload or resource in the tenant, so OneDrive, Teams, Sharepoint etc. So be ready to answer some support calls from other users if Peter was a heavy consumer of externally shared resources.
I do wonder if we should run a script to remove “Microsoft Accounts” monthly from AAD, what do you think? Or prevent them completely as they are a security issue as non business/corporate accounts could access to your resources? But, the tables have turned, as the organisation now has access to the personal Live ID account, as they potentially receive the reset email password.